Introduction
In this article, we explain the issue of misdirected emails, set out some example email data breaches and then highlight how a behaviour change based approach can empower users to protect themselves against this threat.
Accidentally sending an email to the wrong person might seem innocuous. It's a mistake most of us have made without serious consequences. A simple apology can quickly solve the problem. However, when it comes to work emails and confidential information, this “innocuous” mistake can get both the sender and their company in big trouble.
The definition of a misdirected email
According to the DBIR, Misdelivery (or misdirected emails) and other miscellaneous errors are still one of the major causes of data breaches. In industries like Healthcare, these errors are at the top of lists that also include social engineering.
DBIR defines Misdelivery as “people, users, employees sending an email containing sensitive data to the wrong recipient.”
The consequences of these mistakes can be very serious, with companies losing time, money, clients, partners and even facing lawsuits.
What data can be compromised by a misdirected email?
DBIR shows that:
- Personal data is most commonly compromised by such breaches, leading the way with 79%.
- In the healthcare industry, Personal data are exposed in 66% of breaches against 55% of medical data (in the overlapping 21%, they both are).
- Other data includes banking details (13%) and credentials (13%)
Considering that personal data helps build other types of cyber threats, such as more relevant and engaging social engineering attacks, the protection of this kind of information must be a top priority.
Different ways to misdirect emails
As well as sending data to the wrong recipient, misdelivery errors can also occur when the recipients of bulk emails have their names and email addresses exposed to other parties on the list. On 6 September 2019, a London gender identity clinic exposed details of almost 2,000 people on its email list.
The clinic sent out a mass email disclosing to the recipients the email addresses of patients. The unauthorised disclosure of almost 2,000 individuals’ data resulted from email addresses being placed in the ‘To’ field instead of the ‘Bcc’ field; thereby making the email addresses visible to other recipients.
What are the causes of misdirected emails?
Causes of the mistakes appear to be various, like multi-tasking while sending emails, being tired or under pressure, and sometimes our tools let us down, with mistakes caused by cached addresses and email client auto-complete functions being a bit too clever!
How to prevent misdirected emails
We have talked about the problem, now it is time to talk about misdirected email solutions. People will make mistakes, that is guaranteed, but what the team at ThinkCyber has found in their years of experience changing behaviours is that we can gently nudge users at points of risk to double-check, stop and think.
And part of this is giving them the tools to use their email safely. For example, educating about the use of Bcc. We know this is not ground-breaking, but we have noticed that sometimes employees are not completely sure about it, and often email applications hide the Bcc field from the interface, so an extra step is required to enable it.
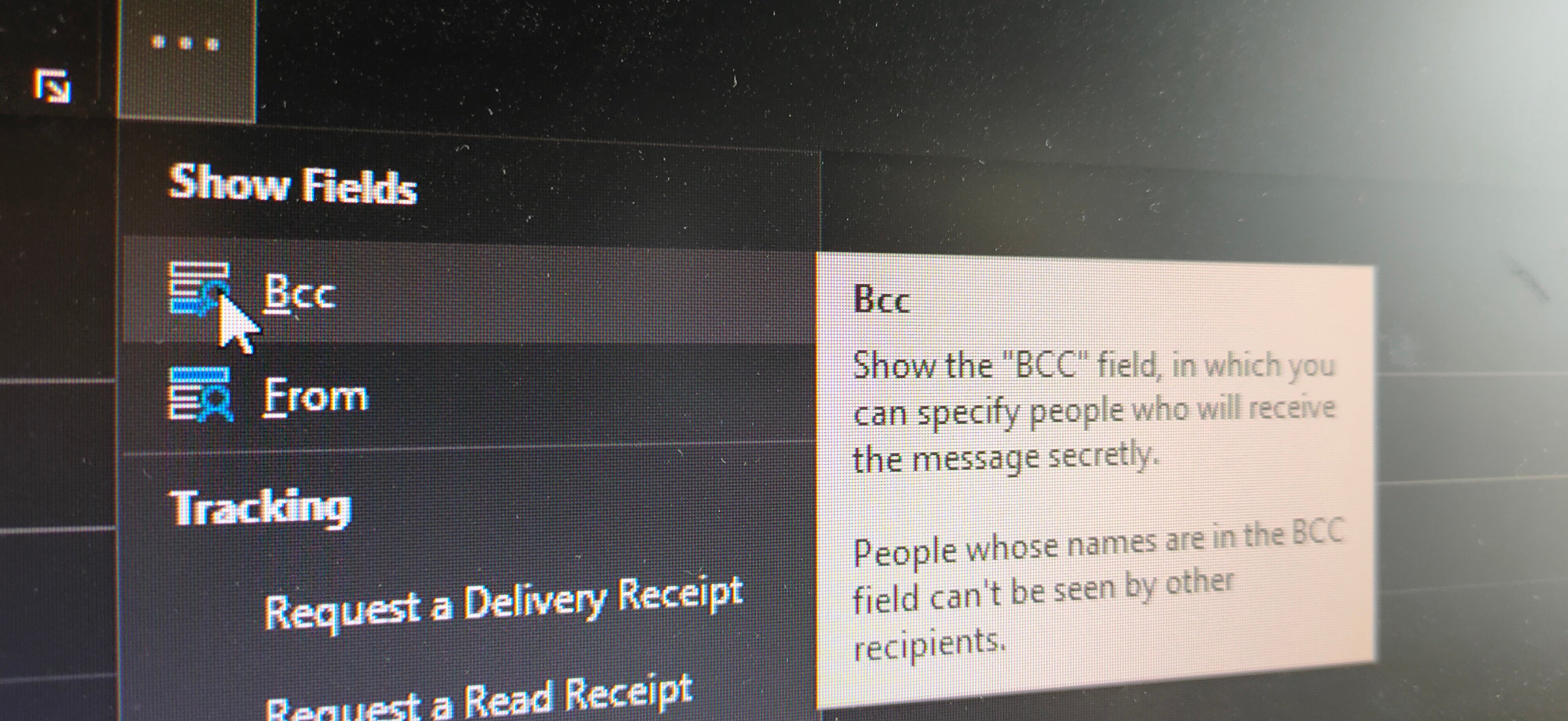
The second solution, which should support the first one, is to send a reminder from time to time. Once people have been trained about a key security issue, the forgetting curve model shows us that they are likely to forget quickly about it, so it is up to us to make sure they remember it. This should reinforce the previous learning by asking people to verify their recipients or double-check they are using the Bcc field if required.
Now you might think: “How do I possibly know when someone in the organisation is about to click send?” or “How can I send a reminder every time someone is writing an email?”.
This is where Redflags® comes in, enabling you to nudge users in a variety of ways, like reminders from time to time when people visit their email. And even better, at the precise point when they add too many To/Cc recipients, attach a file or address an email to a webmail address.
We recommend using this sparingly rather than every time. Nudging little and often encourages a habit to stop and think and be cautious in email.
About Redflags®
ThinkCyber take a behavioural approach to security in their Redflags® software, delivering ongoing and real-time awareness – at the point of risk. In the past years, we've worked with clients across public and private sectors to deliver secure behaviour change and empower staff to protect themselves from cyber threats.
With Redflags® you can deliver the right guidance at the right time, directly to people’s desktops or laptops. So, what about sending a reminder about the correct use of Bcc? This is all possible thanks to Redflags®.
How we can help you tackle the threat of misdirected emails
- Visit the website for more information, tips and live case studies
- Arrange a demonstration of Redflags® – it will take 15 minutes
- Don’t forget to follow us on LinkedIn for up to the minute news

