Think Pieces
How microlearning is redefining the next wave of cyber security training
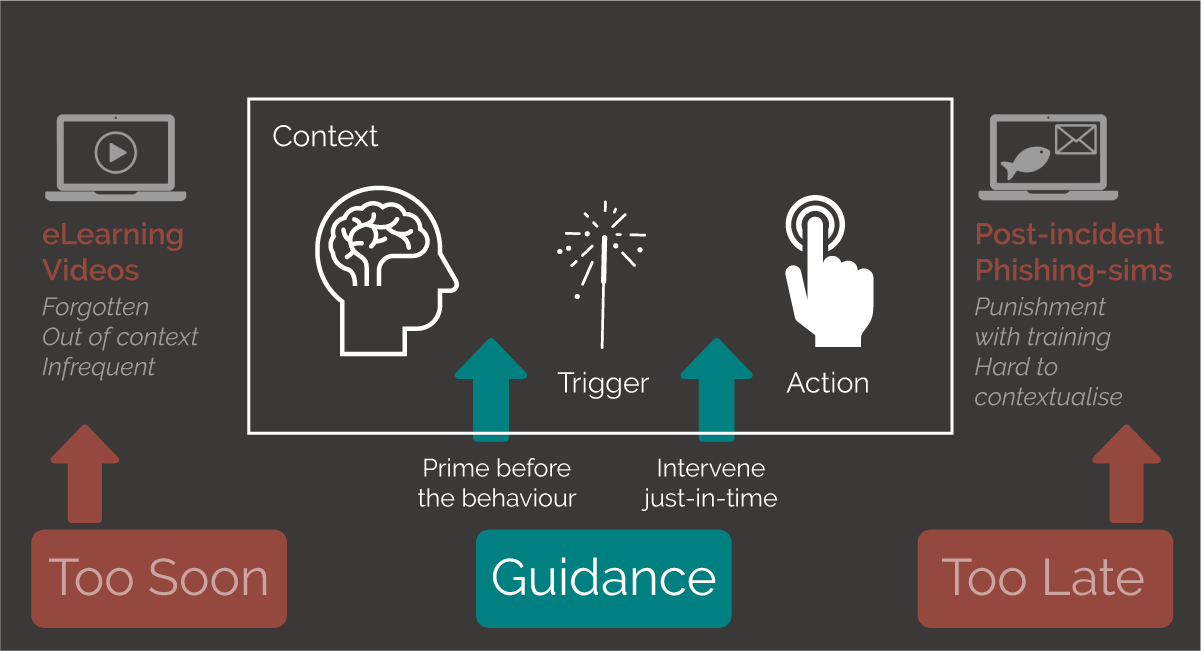
By embracing proven strategies like microlearning, real-time tips, and contextual guidance, cybersecurity can innovate...
Read more